When using wordpress as your content management platform to your site, the nice thing about it is that you can do many things.
How to remove comment section in a page of your theme?
Go to your page.php file and just remove this file.
?php comments_template( '', true ); ?
Thursday, September 30, 2010
Sunday, September 26, 2010
Meeza to Lead Qatari Delegation to Dubai IT Fair
DOHA: Encouraged by the recent study that showed Qatar becoming the leading market for ICT investments in the Middle East, a big local delegation led by MEEZA will participate in the upcoming Gulf Information Technology Exhibition (GITEX) Technology Week in Dubai from October 17 to 21.
Qatari ICT companies will increase its presence four-fold compared to last year at GITEX considered as the largest ICT event in the region to show growth in investments and to attract further business opportunities in the country.
As the major provider of cloud computing services in Qatar, MEEZA has recently won the award for Best New Cloud Services in the Middle East at the Data Centre Strategies Forum, in Abu Dhabi.
James Fanella, MEEZA Vice President for Sales and Marketing, said they are looking forward to develop a strong working relationship with global companies as Qatar’s ICT landscape expands.
“It is important that our clients, stakeholders and the broader public have an opportunity to hear about new and emerging IT solutions, and understand how these technologies are impacting organisations in Qatar and across the region,” Fanella said.
Qatari companies are fast establishing a reputation as drivers of ICT development such as small business solutions, telecoms and cloud computing and the rapidly increasing IT demands in the Middle East are being met by Qatari companies.
The GITEX Technology Week which will take place at Dubai International Convention Center will also provide an essential platform for companies looking to grow into the region.
Abdulla Qassem, Senior Vice President, Dubai World Trade Center, organiser of GITEX, said the event will help more Qatari organisations build business relationships with the global ICT community, which is now prioritising its attention to this part of the world.
Qassem said Qatar is one of the fastest growing economies in the Gulf and the infrastructure and ease of conducting business has made it a key market for international technology companies.
Many leading regional and international companies have confirmed their presence in the event including Amazon, Avaya, BlackBerry (RIM), Cisco Linksys, Comguard, Datel, Yahoo!, Maktoob, Etisalat, Ford, Fujitsu/Netapp, Genius/Edimax, Hitachi, HP, IBM, Kaspersky, Logicom, Microsoft, Monster, Music Master, Nokia, Oracle, Panasonic, Promate, RTA Secureway, Sharp, Symantec, Tandberg, Thuraya, Touchmate, Yahsat, and many more. The Peninsula
Article Source: The Peninsula
Qatari ICT companies will increase its presence four-fold compared to last year at GITEX considered as the largest ICT event in the region to show growth in investments and to attract further business opportunities in the country.
As the major provider of cloud computing services in Qatar, MEEZA has recently won the award for Best New Cloud Services in the Middle East at the Data Centre Strategies Forum, in Abu Dhabi.
James Fanella, MEEZA Vice President for Sales and Marketing, said they are looking forward to develop a strong working relationship with global companies as Qatar’s ICT landscape expands.
“It is important that our clients, stakeholders and the broader public have an opportunity to hear about new and emerging IT solutions, and understand how these technologies are impacting organisations in Qatar and across the region,” Fanella said.
Qatari companies are fast establishing a reputation as drivers of ICT development such as small business solutions, telecoms and cloud computing and the rapidly increasing IT demands in the Middle East are being met by Qatari companies.
The GITEX Technology Week which will take place at Dubai International Convention Center will also provide an essential platform for companies looking to grow into the region.
Abdulla Qassem, Senior Vice President, Dubai World Trade Center, organiser of GITEX, said the event will help more Qatari organisations build business relationships with the global ICT community, which is now prioritising its attention to this part of the world.
Qassem said Qatar is one of the fastest growing economies in the Gulf and the infrastructure and ease of conducting business has made it a key market for international technology companies.
Many leading regional and international companies have confirmed their presence in the event including Amazon, Avaya, BlackBerry (RIM), Cisco Linksys, Comguard, Datel, Yahoo!, Maktoob, Etisalat, Ford, Fujitsu/Netapp, Genius/Edimax, Hitachi, HP, IBM, Kaspersky, Logicom, Microsoft, Monster, Music Master, Nokia, Oracle, Panasonic, Promate, RTA Secureway, Sharp, Symantec, Tandberg, Thuraya, Touchmate, Yahsat, and many more. The Peninsula
Article Source: The Peninsula
Labels:
Dubai,
GITEX Technology Week,
Middle East
Saturday, September 18, 2010
You don't have permission to access /administrator/index.php on this server
Just in case you happen to get this error...
Forbidden
You don't have permission to access /administrator/index2.php on this server.
Additionally, a 404 Not Found error was encountered while trying to use an ErrorDocument to handle the request.
Solution is to edit your .htaccess file by adding this lines.
IfModule mod_security.c
SecFilterEngine Off
SecFilterScanPOST Off
/IfModule
I can't put < > on the above lines so just add it by yourself. If you don't know how, just give a comment and get back to you asap.
Forbidden
You don't have permission to access /administrator/index2.php on this server.
Additionally, a 404 Not Found error was encountered while trying to use an ErrorDocument to handle the request.
Solution is to edit your .htaccess file by adding this lines.
IfModule mod_security.c
SecFilterEngine Off
SecFilterScanPOST Off
/IfModule
I can't put < > on the above lines so just add it by yourself. If you don't know how, just give a comment and get back to you asap.
Labels:
Joomla,
Web Design
Saturday, August 28, 2010
Hiring An IT Consultants
Some IT consultants are specialize in controlling a companies pre-existing IT solutions, while others specialize in the development of IT solutions from scratch. So if you are really looking for information technology management, be sure to ask if the IT company offers a comprehensive controlling strategies. Otherwise, there is no need to waste time on the first consultation with a company that specialized in what you don't need.
Make sure you really need expert IT Management
Outsourcing IT management has become a popular tool for business that some companies do not test if they can manage their own IT management. In some cases, the complexity and scale of enterprise computing solutions require them to hire an expert in the house or outsource to an expert. But in other cases, an enterprise solutions are so simple that can be managed by technical staff. However, always make sure that the dependent instruction provides them with management skills, as there are many horror stories about IT to delegate management to employees who are computer literate.
Find a consultant with experience in your business area
The appointment of a consultant, is like visiting a doctor. To help you with your problem properly diagnosed, you should consult a specialist who has experience working in your large enterprise IT concerns, which usually means hiring a professional who has demonstrated expertise in helping companies like yours. Any business, it may suggest viable solutions for any business. But if your goal is perfection and not workability, only hire a computer company that has good experience.
Determining whether a Consultant who works in house will be more affordable
In the era of outsourcing, the decision to employ a full-time experts in computer consulting instead of outsourcing to a reputable company it will raise some eyebrows for companies, but business wise, there are companies who knows that outsourcing can sometimes be more expensive than the hiring an expert in the house, or even a team of qualified experts. Instead of automatically accede to the idea that outsourcing is equal to the best results, do your research and make sure you do not only include a snapshot of the company.
Examine how a company's payment options agreement with your management requirements
There are management consultants that only accept clients on a contractual basis, while others offer services on pay as you go basis. If you know that outsourcing IT Consultants perform better in the near future, then a contract that is not a bad idea. But the flip side, information management is to hire a pay as you go basis to give greater financial freedom.
Make sure you really need expert IT Management
Outsourcing IT management has become a popular tool for business that some companies do not test if they can manage their own IT management. In some cases, the complexity and scale of enterprise computing solutions require them to hire an expert in the house or outsource to an expert. But in other cases, an enterprise solutions are so simple that can be managed by technical staff. However, always make sure that the dependent instruction provides them with management skills, as there are many horror stories about IT to delegate management to employees who are computer literate.
Find a consultant with experience in your business area
The appointment of a consultant, is like visiting a doctor. To help you with your problem properly diagnosed, you should consult a specialist who has experience working in your large enterprise IT concerns, which usually means hiring a professional who has demonstrated expertise in helping companies like yours. Any business, it may suggest viable solutions for any business. But if your goal is perfection and not workability, only hire a computer company that has good experience.
Determining whether a Consultant who works in house will be more affordable
In the era of outsourcing, the decision to employ a full-time experts in computer consulting instead of outsourcing to a reputable company it will raise some eyebrows for companies, but business wise, there are companies who knows that outsourcing can sometimes be more expensive than the hiring an expert in the house, or even a team of qualified experts. Instead of automatically accede to the idea that outsourcing is equal to the best results, do your research and make sure you do not only include a snapshot of the company.
Examine how a company's payment options agreement with your management requirements
There are management consultants that only accept clients on a contractual basis, while others offer services on pay as you go basis. If you know that outsourcing IT Consultants perform better in the near future, then a contract that is not a bad idea. But the flip side, information management is to hire a pay as you go basis to give greater financial freedom.
Labels:
IT Consultants
Saturday, August 7, 2010
NTLDR is Missing: How You'll Fix it?
We encountered this problem one time and I want to share with how we manage to fix it.
Here was the full error messages that can was seen when the computer starts.
NTLDR is Missing
Press any key to restart
How we fixed it?
1. Insert the Windows XP bootable CD into the computer.
2. When prompted to press any key to boot from the CD, press any key.
3. Once in the Windows XP setup menu press the "R" key to repair Windows.
4. Log into your Windows installation by pressing the "1" key and pressing enter.
5. You will then be prompted for your administrator password, enter that password.
6. Copy the below two files to the root directory of the primary hard disk. In the below example we are copying these files from the CD-ROM drive letter, which in this case is "e." This letter may be different on your computer.
copy e:\i386\ntldr c:\
copy e:\i386\ntdetect.com c:\
7. Once both of these files have been successfully copied, remove the CD from the computer and reboot.
Here is a video so you'll get it more easily.
This solutions will surely work. Goodluck!
Here was the full error messages that can was seen when the computer starts.
NTLDR is Missing
Press any key to restart
How we fixed it?
1. Insert the Windows XP bootable CD into the computer.
2. When prompted to press any key to boot from the CD, press any key.
3. Once in the Windows XP setup menu press the "R" key to repair Windows.
4. Log into your Windows installation by pressing the "1" key and pressing enter.
5. You will then be prompted for your administrator password, enter that password.
6. Copy the below two files to the root directory of the primary hard disk. In the below example we are copying these files from the CD-ROM drive letter, which in this case is "e." This letter may be different on your computer.
copy e:\i386\ntldr c:\
copy e:\i386\ntdetect.com c:\
7. Once both of these files have been successfully copied, remove the CD from the computer and reboot.
Here is a video so you'll get it more easily.
This solutions will surely work. Goodluck!
Labels:
Tips,
Troubleshooting,
Windows XP
Research in Motion Reaches Deal With Saudi Arabia
Research In Motion has remained tight-lipped Saudi officials said the company has reached a tentative agreement that would allow the Government of the Kingdom "access to encrypted data of BlackBerry users to avoid the ban on mobile phones in the country.
The agreement is to place a server within Saudi borders, an official told the Associated Press on Saturday. The move likely would leave messages for control of the government and to dispel the concern that Blackberry could be used for criminal purposes " said Mohammed al-Bandar, a senior Saudi Communications and Information Technology Commission.
The agreement is to place a server within Saudi borders, an official told the Associated Press on Saturday. The move likely would leave messages for control of the government and to dispel the concern that Blackberry could be used for criminal purposes " said Mohammed al-Bandar, a senior Saudi Communications and Information Technology Commission.
Labels:
Blackberry,
Smartphones
Monday, August 2, 2010
BlackBerry Users in UAE and Saudi May Have Services Cut
DUBAI/RIYADH (Reuters) - More than a million BlackBerry users may have key services in Saudi Arabia and the UAE cut off after authorities stepped up demands on smartphone maker Research In Motion for access to encrypted messages sent over the device.
BlackBerry's Messenger application has spread rapidly in the Gulf Arab region but because the data is encrypted and sent to offshore servers, it cannot be tracked locally.
"Certain BlackBerry services allow users to act without any legal accountability, causing judicial, social and national security concerns," the United Arab Emirates' Telecommunications Regulatory Authority (TRA) said in a statement.
The UAE said it would suspend BlackBerry Messenger, email and Web browser services from October 11 until a fix was found, while industry sources said Saudi Arabia had ordered local telecom companies to freeze Messenger this month.
Sunday's moves cap wrangling with regulators over the issue, which first surfaced in 2007.
India raised similar security concerns last week, and Bahrain in April warned against using BlackBerry Messenger to distribute local news. As far back as 2007, France cautioned officials about using the services.
Indian security officials were concerned that BlackBerry's encrypted data could be used to coordinate acts against the state. They have clamped down on mobile phone operators in the wake of 2008 attacks that killed 166 people in Mumbai.
The UAE, home to Gulf financial hub Dubai, said it would halt BlackBerry services until an "acceptable solution" was developed and applied.
Users of the device said that could mean disruptions for companies and individuals who rely on the services, including almost 700,000 in Saudi Arabia and some 500,000 in the UAE.
"It's a final decision but we are continuing discussions with them," Mohammed Al Ghanem, director general of the UAE's TRA, told Reuters.
BlackBerry's Messenger application has spread rapidly in the Gulf Arab region but because the data is encrypted and sent to offshore servers, it cannot be tracked locally.
"Certain BlackBerry services allow users to act without any legal accountability, causing judicial, social and national security concerns," the United Arab Emirates' Telecommunications Regulatory Authority (TRA) said in a statement.
The UAE said it would suspend BlackBerry Messenger, email and Web browser services from October 11 until a fix was found, while industry sources said Saudi Arabia had ordered local telecom companies to freeze Messenger this month.
Sunday's moves cap wrangling with regulators over the issue, which first surfaced in 2007.
India raised similar security concerns last week, and Bahrain in April warned against using BlackBerry Messenger to distribute local news. As far back as 2007, France cautioned officials about using the services.
Indian security officials were concerned that BlackBerry's encrypted data could be used to coordinate acts against the state. They have clamped down on mobile phone operators in the wake of 2008 attacks that killed 166 people in Mumbai.
The UAE, home to Gulf financial hub Dubai, said it would halt BlackBerry services until an "acceptable solution" was developed and applied.
Users of the device said that could mean disruptions for companies and individuals who rely on the services, including almost 700,000 in Saudi Arabia and some 500,000 in the UAE.
"It's a final decision but we are continuing discussions with them," Mohammed Al Ghanem, director general of the UAE's TRA, told Reuters.
Labels:
IT news,
Smartphones
Tuesday, June 22, 2010
Upgrade to Windows 7 Professional Special Offer - Save 255 Dhs
 Microsoft and Information Technology Dubai company UnlimITed IT have teamed together with this special offer to upgrade windows XP and Vista computers to Windows 7 Professional. To add to this great deal Microsoft are giving away 100 free T-shirts and Mugs!
Microsoft and Information Technology Dubai company UnlimITed IT have teamed together with this special offer to upgrade windows XP and Vista computers to Windows 7 Professional. To add to this great deal Microsoft are giving away 100 free T-shirts and Mugs!The Deal
- Windows 7 Professional License - Special Microsoft reduced price of 520 Dhs per license
- Installation and Migration of Data - Special UnlimITed reduced price of 175 Dhs per license (Optional)
- Delivered and Installed at your Office
- Bulk Purchase savings for 10+ Licenses
Contact UnlimITed Sales for a quotation now - sales@unlimited-it.ae or call 04-2694567.
For more information about the great benefits check out the information below or contact UnlimITed!
Why should I upgrade to Windows 7?
Designed to meet the needs of small and midsize businesses, the Windows 7 Professional operating system delivers a powerful combination of innovation, improved performance, and productivity. At UnlimITed we're ready to help focus on what matters most, your business, by providing you with a solution that:
- Works the way you want. Fast, reliable, and compatible, Windows 7 Professional delivers a solid foundation for running a business in today's competitive environment.
- Helps you get more done. Find what you need quickly, easily connect to your networks, and be more productive-whether you're at work, at home, or on the road.
- Safeguards your work. Keep your business up and running with new security and recovery options that help prevent security threats and data loss.
Labels:
IT news
Monday, May 3, 2010
How to Set Safari as Your Default Browser in MAC?
Frankly speaking, I don't use MAC . So there are still many things I need to learn when it comes to troubleshooting from simple to complex. Though I know there are already many article post about it, it is still good to experience it myself. Yesterday, I was with my colleague in a client to fix issues regarding MAC.
 How to set up Safari as your default browser? Here is an easy way how to do it. Download Safari browser in case you haven't installed it yet.
How to set up Safari as your default browser? Here is an easy way how to do it. Download Safari browser in case you haven't installed it yet.
Change Your Default Browser on Your Computer
 How to set up Safari as your default browser? Here is an easy way how to do it. Download Safari browser in case you haven't installed it yet.
How to set up Safari as your default browser? Here is an easy way how to do it. Download Safari browser in case you haven't installed it yet.Change Your Default Browser on Your Computer
- Choose 'System Preferences' from the Apple pull down menu on your desktop.
- Click on 'Internet' under the 'Internet and Network' section.
- Choose the option 'Web' from the list of headings.
- Choose Safari from the list of available Web browsers in the pull down menu.
- Close the 'System Preferences' window and restart your computer.
- Open up the Safari Web browser.
- Choose 'Preferences' from the Safari pull down menu.
- Click on the heading 'General.'
- Choose Safari from the pull down list of available Web browsers next to where it says 'Default Web Browser.'
- Close the Safari 'Preferences' window and restart your computer.
Labels:
MAC,
Troubleshooting
Wednesday, April 21, 2010
Network Bandwidth Monitoring Tool
Do you need help identifying your biggest bandwidth abusers and malicious applications running on your network? Then try Axence NetTools.
Axence NetTools is a free and comprehensive set of host monitoring, network scanning, security and administration tools, all with a highly intuitive user interface.
Axence Net Tools monitors the availability of several hosts and their response times. You can set several thresholds so that NetTools will notify you by e-mail, message or sound in case of host not responding or slower connection. NetWatch provides very clear real-time and historical charts of a response time and percentage of packets lost. As with all the other tools, you can export this information as text, Excel and html files.
Lists exhaustive system information from Windows computers: running processes & services, registry, event log, disk, memory & CPU information, and much more. You can also define your own queries.
There are other things which you will find useful in monitoring your network bandwidth using Axence NetTools.
You can download the tool here. And if you are looking for network management services Dubai or IT services, visit Unlimited.
Axence NetTools is a free and comprehensive set of host monitoring, network scanning, security and administration tools, all with a highly intuitive user interface.
Axence Net Tools monitors the availability of several hosts and their response times. You can set several thresholds so that NetTools will notify you by e-mail, message or sound in case of host not responding or slower connection. NetWatch provides very clear real-time and historical charts of a response time and percentage of packets lost. As with all the other tools, you can export this information as text, Excel and html files.
Lists exhaustive system information from Windows computers: running processes & services, registry, event log, disk, memory & CPU information, and much more. You can also define your own queries.
There are other things which you will find useful in monitoring your network bandwidth using Axence NetTools.
You can download the tool here. And if you are looking for network management services Dubai or IT services, visit Unlimited.
Labels:
Network Solutions
Wednesday, April 7, 2010
How to Add Contacts in Microsoft Outlook?
To create a contact in Microsoft Outlook, follow the below steps.

 There is an easy way to open the Address Book window. Right click on the email address that you want to add then choose Add to Outlook Contacts.
There is an easy way to open the Address Book window. Right click on the email address that you want to add then choose Add to Outlook Contacts.
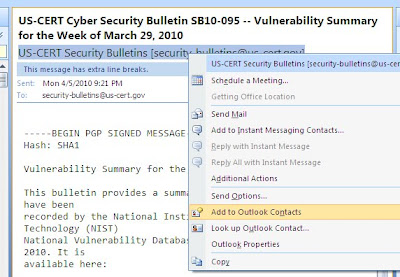
It's so easy, isn't it?
- Open Microsoft Outlook
- Click the Tools menu and then Address Book or press CTRL + Shift + B.

- In the Address Book window, click the New button and then New contact, click File and then New contact, or press CTRL + N.
- In the Properties window, type the name and e-mail of your contact as well as any other contact information you need to remember such as phone number and address.
 There is an easy way to open the Address Book window. Right click on the email address that you want to add then choose Add to Outlook Contacts.
There is an easy way to open the Address Book window. Right click on the email address that you want to add then choose Add to Outlook Contacts.
It's so easy, isn't it?
Labels:
Email How To's,
Microsoft Outlook
Sunday, April 4, 2010
Troubleshooting Fatal Error 2753 during Installation of HP Printer

The good thing about being an IT in Dubai or in any places is that you will learn many things and solve IT issues which we do not encounter all the time. And having a different specialization,
I am always excited to go out with them specially when it comes to troubleshooting.
This time, we were face with Fatal Error 2753 during installation of HP printer.
Since the client no longer has the installation cd of the HP Laserjet 3033 printer, we downloaded the driver from HP website.
After the driver was downloaded, we have run the installation but but got an error 2753. My colleague suspects that there are files which are either missing or were not properly installed. And after going through some websites looking for answer, we found out that indeed there were .dll files that needs to be removed.
Cause of Fatal Error 2753:
Certain HP services (and associated DLL files) were somehow partially/improperly installed. (Possibly, from a previous failed install?)
The Windows services (files) are:
Pml Driver HPZ12 (C:\Windows\System32\HPZipm12.dll)
Net Driver HPZ12 (C:\Windows\System32\HPZinw12.dll)
The existence of these 2 files in the System32 directory was causing this error in my situation. Somehow, the installation script was not identifying that these files were already installed (or improperly installed) and failing to properly set them to be installed again.
Solution to Fatal Error 2753:
Steps:
1) Check to make sure that the 2 Windows services above are not running (or not installed).
2) Rename/delete the 2 associated service DLL files (this will only be possible once the services are stopped)
3) Run the installation again.
Labels:
HP,
Printers,
Troubleshooting
Monday, March 8, 2010
Win32/Agent stealing personal data on the rise; Conficker still No. 1 Threat
Win32/Conficker is the most widespread computer threat in the world with a share of 9,62% of all detected forms of malware. The data si based on ThreatSense.Net®, ESET’s in-the-cloud malware detection system collecting data from users of ESET Smart Security and ESET NOD32 Antivirus.
Among the top three infiltrations, globally were INF/Autorun with 7,24% of all infiltrations and Win32/PSW.OnLineGames with 6,20%. Both mentioned classifications of malware encompass mostlyTrojans exploiting the Windows OS autorun function (autorun.inf) or malware designed for stealing sensitive information form PC online games.
The fourth most widespread threat worldwide is Win32/Agent with a share of 3,57%, and still growing month by month, approaching the levels it has reached during the summer of 2009. ESET classifies this threat as a generic form of malware in the cattegory of PC data stealer. Win32/Agent covers a broad range of infiltrations utilizing a multitude of vectors. In Europe, it has even placed among top three infiltrations with a share of 4%. ESET advises computer users to ensure that they stay protected using an effective antivirus software, administer operating system patches as they are issued as well as other security updates of potentially vulnerable programs. INF/Conficker is the next most prevalent form of malware, placing fifth in ESET’s ranking. INF/Conficker utilizes the same means of propagation as INF/Autorun ̶ via autorun.inf. function. Throughout the month of February, this threat has accounted for 1,71% of the total of global infiltrations.
EUROPE, MIDDLE EAST and AFRICA (EMEA)
Similarly as is the case with teh rest of the world, Win32/Conficker represents the most frequently encountered type of malware in the EMEA region. It afflicts all corners of the EMEA region ̶ Russia (15,31%) Ukraine (23,06%), Hungary (6,50%), the Czech Republic (4,34%), Slovenia (4%), Germany (6,84%), Great Britain (8,17%), Finland (7,60%), Egypt (11,65%) and South Africa (11,91%).
Trojans INF/Autorun have been the dominant form of malware with high occurance in Israel (6,11%), Lithuania (4,66%), Spain (9,55%), Portugal (5,3%), but also in France (7,85%) and Norway (4,37%).
Win32/PSW.OnLineGames is among the most frequently detected malware on users' computers in Slovakia (8,90%), Poland (15,39%) and Turkey (10,66%) .
Win32/Agent is the number one threat in Austria (4,54%); also registering high rate of occurrence in other countries, such as Hungary (3,70%), Poland (2,84%) , Sweden (2,39%), and Denmark (4,16%).
Among the top three infiltrations, globally were INF/Autorun with 7,24% of all infiltrations and Win32/PSW.OnLineGames with 6,20%. Both mentioned classifications of malware encompass mostlyTrojans exploiting the Windows OS autorun function (autorun.inf) or malware designed for stealing sensitive information form PC online games.
The fourth most widespread threat worldwide is Win32/Agent with a share of 3,57%, and still growing month by month, approaching the levels it has reached during the summer of 2009. ESET classifies this threat as a generic form of malware in the cattegory of PC data stealer. Win32/Agent covers a broad range of infiltrations utilizing a multitude of vectors. In Europe, it has even placed among top three infiltrations with a share of 4%. ESET advises computer users to ensure that they stay protected using an effective antivirus software, administer operating system patches as they are issued as well as other security updates of potentially vulnerable programs. INF/Conficker is the next most prevalent form of malware, placing fifth in ESET’s ranking. INF/Conficker utilizes the same means of propagation as INF/Autorun ̶ via autorun.inf. function. Throughout the month of February, this threat has accounted for 1,71% of the total of global infiltrations.
EUROPE, MIDDLE EAST and AFRICA (EMEA)
Similarly as is the case with teh rest of the world, Win32/Conficker represents the most frequently encountered type of malware in the EMEA region. It afflicts all corners of the EMEA region ̶ Russia (15,31%) Ukraine (23,06%), Hungary (6,50%), the Czech Republic (4,34%), Slovenia (4%), Germany (6,84%), Great Britain (8,17%), Finland (7,60%), Egypt (11,65%) and South Africa (11,91%).
Trojans INF/Autorun have been the dominant form of malware with high occurance in Israel (6,11%), Lithuania (4,66%), Spain (9,55%), Portugal (5,3%), but also in France (7,85%) and Norway (4,37%).
Win32/PSW.OnLineGames is among the most frequently detected malware on users' computers in Slovakia (8,90%), Poland (15,39%) and Turkey (10,66%) .
Win32/Agent is the number one threat in Austria (4,54%); also registering high rate of occurrence in other countries, such as Hungary (3,70%), Poland (2,84%) , Sweden (2,39%), and Denmark (4,16%).
Monday, February 22, 2010
How to join a windows xp machine on a domain
For security purposes., most companies joins each of their machines to the domain they are using. This controls what users can and can't do on a computer system. Group policy is more often seen in use for enterprise environments, it is also common in schools, smaller businesses and other kinds of smaller organizations. Group Policy is often used to restrict certain actions that may pose potential security risks, for example: to block access to the Task Manager, restrict access to certain folders, disable the downloading of executable files and so on.
How to join a windows xp machine on a domain
To change a computer name and to join a domain or a workgroup, first you need to locate the System Properties. You can find this through the following:
How to join a windows xp machine on a domain
To change a computer name and to join a domain or a workgroup, first you need to locate the System Properties. You can find this through the following:
- Right-click My Computer, and then click Properties.
- Click Start, click Run, type sysdm.cpl, and then click OK.
- Click Start, click Control Panel, and then click System.
- Now click on the Computer Name tab, and then click Change.
- Type the new computer name in the Computer name dialog box.
- Type the domain name on the dialog box.
- More to change the primary Domain Name System (DNS) suffix.
- OK three times, and then restart your machine.
Labels:
Domain,
Windows XP,
Windows XP How To's
Sunday, February 7, 2010
This website has been reported as unsafe
Today, I was with a client which was reported to have issues with opening websites. Any websites she was trying to open gives her a page where it says "This website has been reported as unsafe".

This website has been reported as unsafe is a browser hijacker that will be presented to users infected with a fraudulent security application. This program is promoted through the use of malware that will install it on your computer without your permission. In order to protect itself, this program will automatically attempt to terminate security programs that may help to remove it. When installed, Personal Security will be configured to start automatically when Windows starts. Once started, it will scan your computer and display a variety of infections, but will state that it will not remove them unless you first purchase the program. In reality, the infections it finds are either fake or legitimate programs that if deleted could cause problems with the proper operation of Windows. Therefore, please do not act upon any of the files it states are infections.

The web page read:
Initially, when I encounter laptops or desktop with virus issues, I use Malwarebytes to permanently delete viruses.
What you should do is download Malwarebytes' Anti-Malware or MBAM which you will find here and install it to your machine. Since you can not use your machine to open websites, you need to use another machine to download this software and save it to your desktop.
Once you are finish installing malwarebytes, it is recommended to run on a Full Scan. When the scan is finished, malwarebytes will give you a message box that says that the scan was completed successfully and will give you the option to show the results.
A screen displaying all the malware that the program found will be shown. You will see that the boxes beside the malwares are already thicked so what you need to do is to click Remove Selected and this will delete all malwares and spywares on your machine. You will be prompted to reboot your machine in order to remove some of them. Now your machine is free from malware and you will no longer see error "This website has been reported as unsafe".
Any questions please feel free to ask by using the comment form below.

This website has been reported as unsafe is a browser hijacker that will be presented to users infected with a fraudulent security application. This program is promoted through the use of malware that will install it on your computer without your permission. In order to protect itself, this program will automatically attempt to terminate security programs that may help to remove it. When installed, Personal Security will be configured to start automatically when Windows starts. Once started, it will scan your computer and display a variety of infections, but will state that it will not remove them unless you first purchase the program. In reality, the infections it finds are either fake or legitimate programs that if deleted could cause problems with the proper operation of Windows. Therefore, please do not act upon any of the files it states are infections.

The web page read:
This website has been reported as unsafeHow to Remove This website has been reported as unsafe:
We strongly recommend to discontinue the use of this website.
Activate my Web Protection software.
This website has been reported to Microsoft for containing threats that might steal personal of financial information from your computer.
Initially, when I encounter laptops or desktop with virus issues, I use Malwarebytes to permanently delete viruses.
What you should do is download Malwarebytes' Anti-Malware or MBAM which you will find here and install it to your machine. Since you can not use your machine to open websites, you need to use another machine to download this software and save it to your desktop.
Once you are finish installing malwarebytes, it is recommended to run on a Full Scan. When the scan is finished, malwarebytes will give you a message box that says that the scan was completed successfully and will give you the option to show the results.
A screen displaying all the malware that the program found will be shown. You will see that the boxes beside the malwares are already thicked so what you need to do is to click Remove Selected and this will delete all malwares and spywares on your machine. You will be prompted to reboot your machine in order to remove some of them. Now your machine is free from malware and you will no longer see error "This website has been reported as unsafe".
Any questions please feel free to ask by using the comment form below.
Labels:
Malwarebytes,
Virus Issues
Subscribe to:
Posts (Atom)